75M Attack on $5B Giant: What Are They Up To?
Monero Faces the Most Dangerous Month Ever, Targeting $5 Billion Whale
If the cryptocurrency world is known for anything, it's never lacking in drama. This time, however, the spotlight is on Monero.
This wasn't a sudden attack but a premeditated show of force that was announced publicly a month in advance—a well-prepared hashrate duel. The attackers even announced their intention to "challenge the Monero network between August 2 and August 31." Their goal was to achieve a rare feat in the blockchain world: control over 51% of the hashrate of a privacy coin network with a market cap exceeding $5 billion.
Today, the attackers claim to have achieved this goal.
This Was a Long-Planned Attack
As we all know, in a blockchain network, all transactions must be validated by miners in a process known as "mining." Miners' computational power, or hashrate, determines their chances of mining a new block and receiving a reward.
Monero is no different.
However, unlike other cryptocurrencies, Monero has a design that prevents large mining pools from taking control—it does not support Application-Specific Integrated Circuits (ASICs), and mining can only be done with a CPU or GPU on a regular computer. This rule was intended to prevent miners from centralizing in a few large pools, allowing anyone theoretically to mine with their computer and making the network more fair and decentralized.
Yet, this mechanism also presents an idealized attack vector: rapidly renting or mobilizing a large number of ordinary servers (such as cloud resources, idle PCs, mining rigs). And that's precisely what the attackers did in this case.
Now, let's look at the orchestrator of this long-planned attack, known as Qubic.
The mastermind behind this operation is Qubic, an independent blockchain project not created to attack Monero. Led by Sergey Ivancheglo (aka Come-From-Beyond), a co-founder of IOTA and a seasoned crypto developer, Qubic utilizes a mechanism called "Useful Proof of Work" (UPoW). This mechanism enables miners' hashrate to not only solve mathematical problems but also train their AI system, "Aigarth," creating a dual-purpose system.
So why did Qubic decide to associate itself with Monero and launch a hashrate "war" against it?
In fact, this was a "economic demonstration" by Qubic to showcase its UPoW model capability. Starting from May 2025, it attracted a large number of miners by using its network hashrate for Monero CPU mining, allowing miners to mine Monero and earn $QUBIC tokens simultaneously. The mined Monero was sold for stablecoins, which were then used to repurchase and burn Qubic coins, creating a self-reinforcing economic cycle.
After Qubic announced its intention to "challenge" the Monero network from August 2 to August 31, some members of the Monero community began monitoring the chain around the clock. One person on Reddit stated that they were watching every block, especially keeping an eye out for "orphan blocks." Initially, everything was normal, but one early morning, they noticed a chain reorganization. Chain reorgs are not uncommon in the Monero network, such as when two miners mine a block simultaneously and the system selects one while discarding the other. However, the timing of this reorg was suspicious and seemed to be related to Qubic testing its ability to insert alternative blocks and fork the blockchain. Although the alternative block was eventually rejected, it also indicated Qubic's testing in action.
Monero Block Status
The monitors also discovered that Monero was supposed to produce a block every two minutes, but the block generation speed had recently increased significantly, suggesting that the network had detected signs of pressure from a potential attack. This convinced them that Qubic was indeed causing some kind of disruption. Another participant pointed out that the only orphan block that appeared was just 12 hours before Qubic publicly claimed to launch the attack.
In terms of mining power data, the community also observed that in early August, Qubic stopped reporting its hashrate to public mining pool statistics websites, making it impossible for outsiders to see their actual mining capability directly. Some speculated that this might be to hide peak hashrate, create opacity, and display more favorable numbers through their controlled website. A member of the Monero core team analyzed that their hashrate was not constant but regularly switched between peaks and valleys, posing a more threatening "switching" pattern than stable mining.
The planned attack by Qubic to "flex its muscles" resulted in: between May and July, Qubic held close to 40% of Monero's network hashrate. By August, Qubic claimed to have reached 52.72%, directly surpassing the 51% "control threshold"—meaning that it was technically capable of chain reorgs, double-spend attacks, or transaction censorship. Qubic claimed this was to simulate potential attacks the Monero network might face and identify security vulnerabilities early.
Is Qubic Actually a Scam?
So did Qubic really successfully execute a 51% attack? Many still remain skeptical, believing it was merely a carefully orchestrated marketing deception.
@VictorMoneroXMR raised doubts with the screenshot below. While other Monero mining pools were showing a total hashrate of 4.41 GH/s and the network's total hashrate was 5.35 GH/s, Qubic's data dashboard displayed a hashrate of 2.45 GH/s under the same network hashrate, which clearly didn't add up. It is possible that Qubic's data dashboard did not account for its own hashrate in the network. Adjusting for this assumption would mean Qubic's actual hashrate was only about 30% of the total.
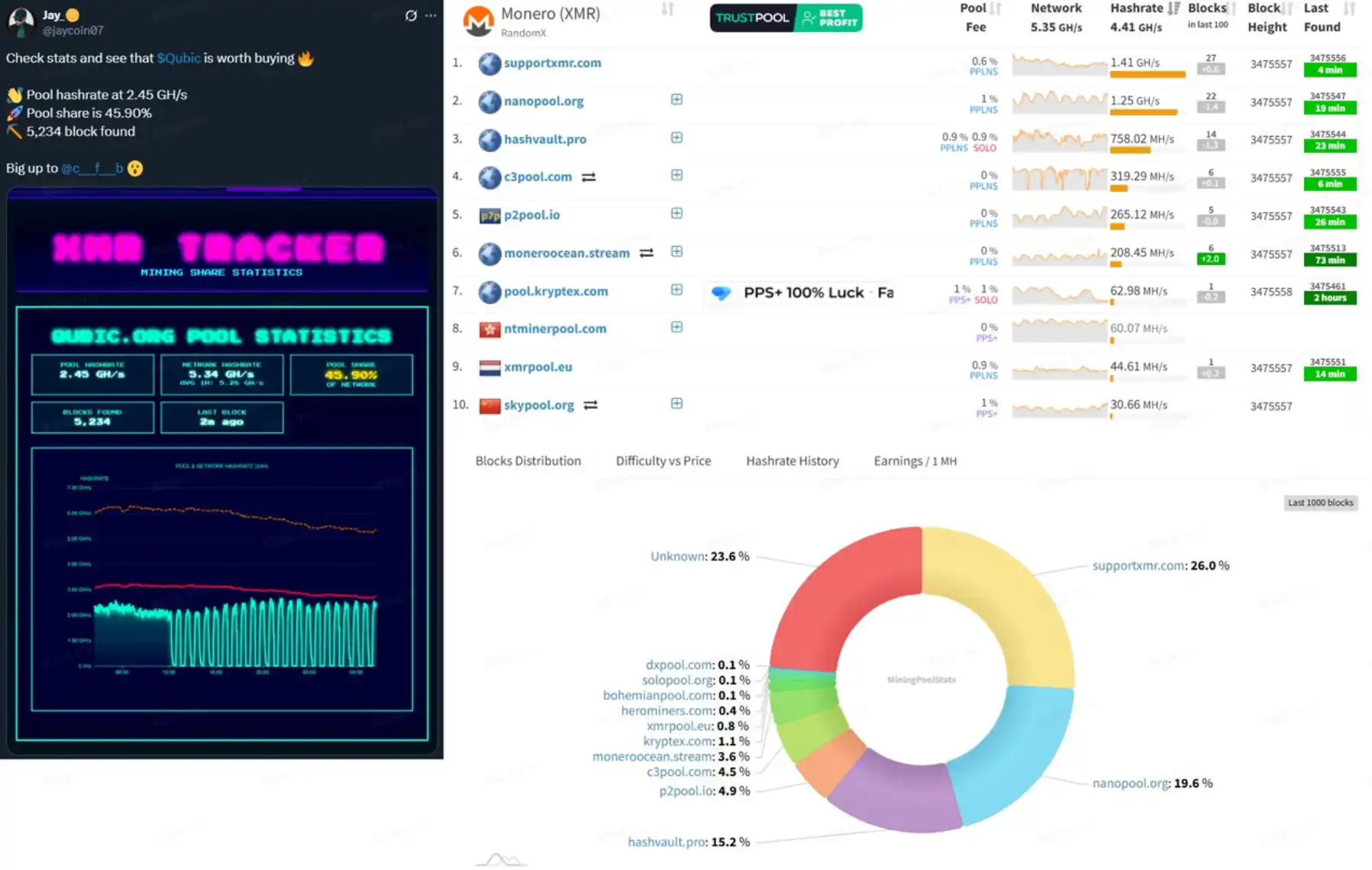
Aside from the data discrepancy, the most direct on-chain evidence so far is that Monero experienced a 6-block chain reorganization, but this still does not definitively prove that Qubic had the capability to launch a 51% attack.
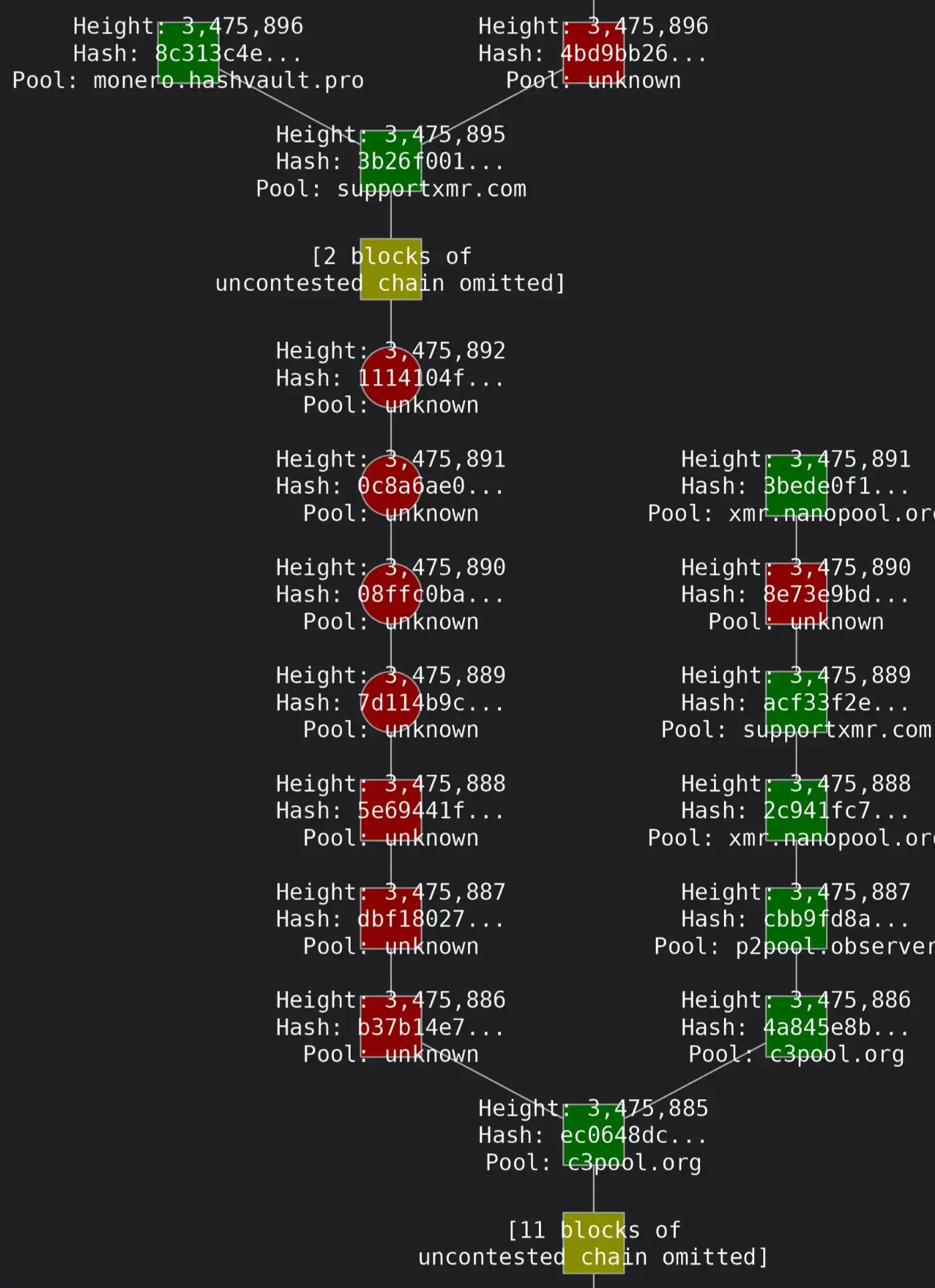
This observation was also corroborated in a real-time block monitoring thread on the Monero Reddit community.
Throughout the entire Qubic challenge period, the community did not see persistent, significant orphan block increases or chain reorganizations, only one suspicion of reorg, with the replacement block being rejected. Core developers and the community observed that Qubic had at times neared or slightly exceeded 50% hashrate (Qubic claimed to have reached 52.72%), even though exceeding 51% for a short period, such as a few minutes or blocks, may not be sufficient to carry out an effective attack.
In other words, there is currently no evidence that they stably maintained over 51% for a long enough duration to successfully launch an attack.
The current consensus in the Monero community is that while Qubic may have briefly exceeded 51%, they did not execute a successful attack, resembling more of a hashrate demonstration and psychological warfare. The attacking party may have showcased exaggerated percentage screenshots on their website to create the impression of having control over the network.
Losing $75 Million to Make $100k Loss on Trade?
The cost of attacking Qubic has also sparked a lot of discussion on social media platforms.
The Monero community's analysis generally believes that maintaining the current computational power held by Qubic would be extremely costly. Based on the current network difficulty, the daily block reward value of the Monero network is approximately $150,000. If an attacker wanted to sustain more than 50% of the network's total computational power, it would mean they would need to produce blocks equivalent to half or more of the entire network daily. The hardware, electricity, and maintenance costs for this portion would be exorbitant.
According to the calculation by Yu Xian, the founder of the security company SlowMist, the cost of such an attack could be as high as $75 million per day, a figure that is almost impossible to recoup through pure speculative mining.
Since this number is excessively high, let's analyze it from another perspective. Let's first look at Crypto51, a website specifically designed to estimate the cost of a 51% attack for various PoW coins. For some mainstream or mid-market cap coins, it provides a reference for the cost of renting hash power per hour, such as Ethereum Classic (market cap of several hundred million dollars): approximately $11,563 per hour; Litecoin: approximately $131,413 per hour.
Although Crypto51 does not have specific data for Monero, it can be seen that even for a medium-sized PoW network, the cost of an attack is usually far below the level of tens of millions of dollars per day.
Based on a Reddit discussion, a community member attempted to estimate the cost of a CPU PoW (like Monero) attack as follows: assuming the use of an AMD Threadripper 3990X (performance around 64 KH/s), it would require about 44,302 of these CPU machines to achieve 51% of the network. The cost of purchasing the devices alone would be approximately $220 million (44,302 × $5,000). If additional hardware costs, site rentals, and electricity expenses are taken into account, millions of dollars more would need to be invested. The electricity cost is estimated at about $100,000 per day.
So, with a $75 million per day attack cost, how much profit could Qubic make from it?
According to Monero's current tail emission rules, the block time is approximately 2 minutes, and the reward per block is fixed at 0.6 XMR. If Qubic controls more than 51% of the computational power, it means they have the ability to mine all Monero blocks daily, which is approximately 432 XMR.
At the time of writing this article, the price of Monero is around $246. Based on the current Monero price, if Qubic were to monopolize all Monero mining output within a day, they would only be able to profit about $106,000.
According to Qubic's official "Epoch 172 Report," Qubic distributes the Monero it mines in a 50% - 50% ratio, with half used for buyback and burning of $QUBIC, and the other half used for miner incentives. However, miner rewards are still paid in $QUBIC.
In other words, with a market cap of less than $300 million, $QUBIC has the ability to monopolize the mining output of Monero, valued at nearly $4.6 billion. Theoretically, they could go all out, burning $53,000 worth of $QUBIC in a day, and $1.509 million worth of $QUBIC in a month. This is truly insane.
The Counterattack of Monero, an Ongoing Struggle
Therefore, it is widely believed that Qubic's motivation is not just for direct Monero mining profits, but to support a "hash power + token" combined economic model: Qubic does not directly pay miners in fiat currency but rewards them with their own token, $QUBIC, and artificially maintains the token's secondary market price. Once the price stabilizes or even rises, they can exchange a relatively low-cost token issuance for massive real hash power support. The core of this approach is that miners mining Monero in the Qubic mining pool receive rewards in Qubic tokens. If the token price remains high, the miners' nominal income is considerable, naturally attracting them.
In terms of profit models, Qubic itself does not necessarily rely on Monero's block rewards to make money but uses this event to generate hype for its token, increase trading volume and price, and attract more speculative buying.
As long as the market cap and liquidity of Qubic's coin remain sufficient to pay miners, this large-scale hash power occupation can continue. However, this model is built on a highly fragile foundation of trust: if miners believe that the price of Qubic's coin is difficult to sustain, they will collectively sell and exchange it for more stable assets, triggering a price collapse and causing a "race to the exits."
This is a naked, domineering hash power "siphoning," naturally leading to strong dissatisfaction and counterattacks from the Monero community.
Interestingly, during Qubic's attack on Monero, they also suffered from an anonymous attack.
According to Qubic's founder Sergey Ivancheglo (aka Come-From-Beyond), their mining pool faced a DDoS attack (Distributed Denial of Service attack) during this phase. Qubic's data shows that its mining pool's hash rate dropped from around 2.6 GH/s to 0.8 GH/s, a decline of over 70%. Therefore, he believes that someone deliberately disrupted their hash power operation through a network attack.
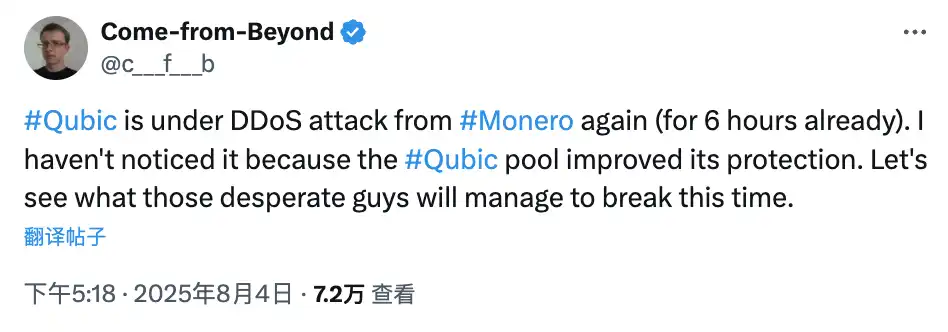
Attacker Qubic Founder Sergey Ivancheglo has stated that he himself has also been attacked
During the accusation process, Ivancheglo even specifically named Monero mining software XMRig's lead developer, Sergei Chernykh (alias sech1), as the mastermind behind the attack. However, sech1 promptly responded, categorically denying any involvement in any illegal attacks: "I am not the only one in the Monero community who is dissatisfied with Qubic's actions. But I will never resort to illegal means like DDoS. Others might."
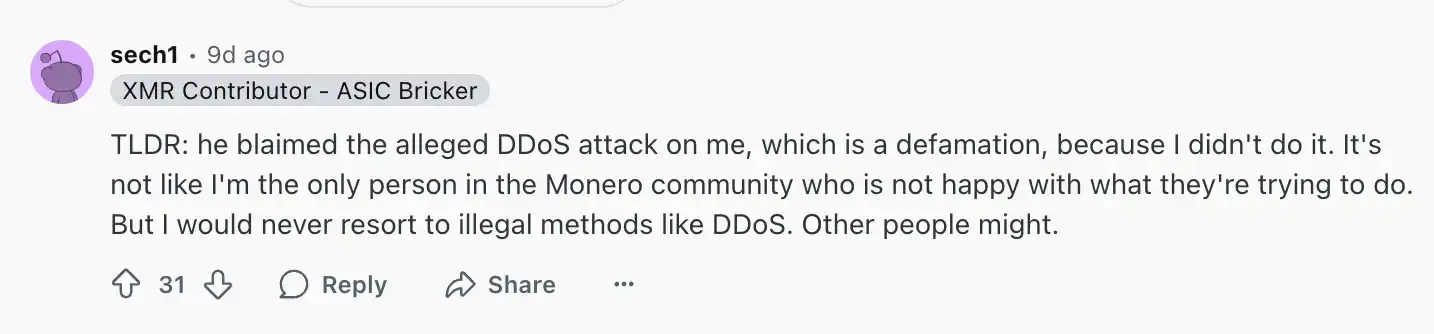
Monero Mining Software XMRig's lead developer has stated, "I am not the only one in the Monero community who is dissatisfied with Qubic's actions"
Meanwhile, discussions within the Monero community seem to be contemplating organizing all Monero supporters to completely eradicate Qubic:
"We need a movement #ShortQubic, they want to provoke us, we can only strike back. After all, the Monero community is bigger." "Where to short Qubic? Why don't we collectively short Qubic Coin, maybe even use leverage? That way, we can completely stifle miners' enthusiasm."
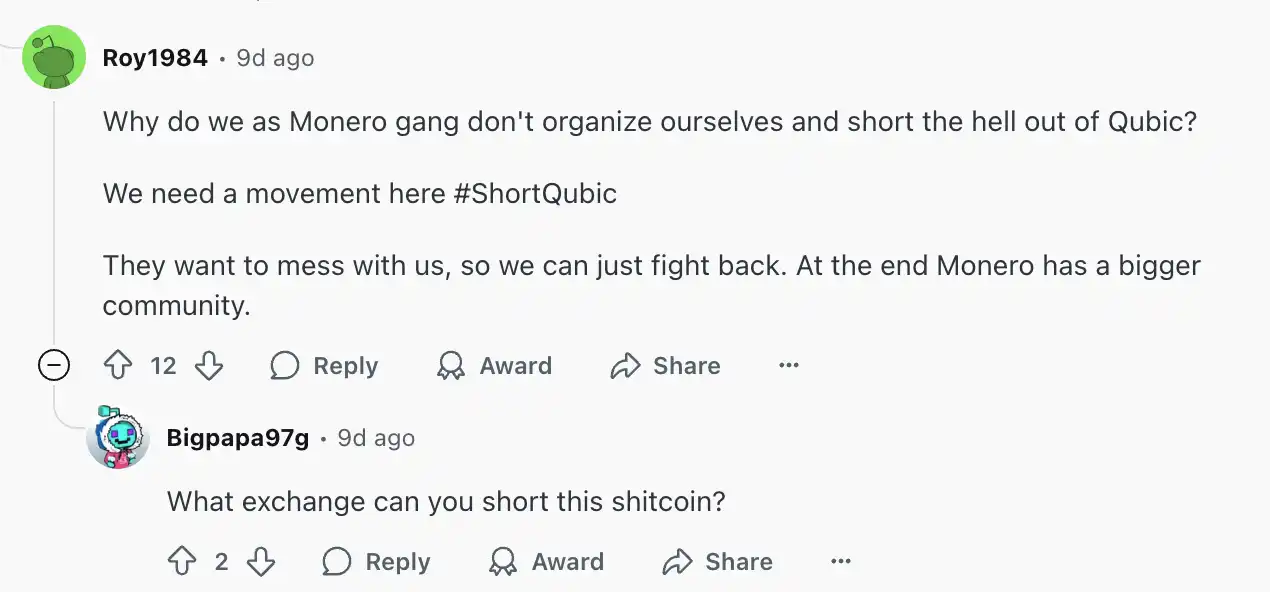
Monero community discusses how to strike back
More interestingly, some members of the Monero community have pointed out that the attack on Monero by Qubic may have ideological reasons.
The Qubic official website shows that the team has many members, but most use aliases, with only two using real names. One is the aforementioned Qubic Founder Sergey Ivancheglo, and the other is Qubic's scientist David Vivancos, who has always advocated for human-machine integration. David Vivancos is described as a "technocratic" who believes in a model of societal governance driven by technical experts and data. This concept has been criticized for being contrary to Monero's pursuit of decentralization, privacy, and community autonomy, and even carries a dystopian undertone.
The battle is not over yet, and the psychological warfare is still ongoing. Next, will the Monero community counter Qubic with technology, finance, or public opinion? And how long can Qubic's "Hashpower Siphon" be sustained? BlockBeats will continue to follow the rhythm.
Disclaimer: The content of this article solely reflects the author's opinion and does not represent the platform in any capacity. This article is not intended to serve as a reference for making investment decisions.
You may also like
XRP ETF Price Crash Explained
XRP Is Not Bitcoin Or Ethereum, Says Canary CEO As XRPC ETF Launches
Strong Staking and BTCFi Boost Starknet Toward the Next $0.30 Target

IOTA Introduces Industry-Agnostic Trust Framework for Verifiable Digital Assets

