Author | Shisi Jun
1. Preface
In the blink of an eye, I have already been working in the wallet track for 4 years. Many people think that the wallet track in 2025 has already solidified, but this is not the case—it is surging beneath the surface. This year:
· Coinbase newly released the CDP wallet, built on TEE technology;
· Binance's MPC wallet introduced key sharding custody into the TEE environment;
· Bitget just launched the social login feature last week, with TEE as the underlying custodian;
· OKX Wallet launched smart account features based on TEE;
· MetaMask and Phantom introduced social login, which is essentially key sharding and encrypted storage.
Although there haven't been any dazzling new players this year, existing players have undergone dramatic changes in ecological positioning and underlying technical architecture.
This transformation stems from drastic changes in the upstream ecosystem.
With the comprehensive decline of the BTC and inscription ecosystem, many wallets have begun to reposition themselves as "entry points" to take on emerging tracks such as Perps (perpetual contracts), RWA (stock-like assets), and CeDeFi (a combination of centralized and decentralized finance).
This transformation has actually been brewing for many years. Follow this article as we delve into those flowers blooming in the dark, and their impact on future users.
2. Review of the Development Stages of the Wallet Track
Wallets are a rare rigid-demand product in the blockchain industry and, apart from public chains, are the first entry-level applications to break through 10 million users.
2.1 First Stage: Single-Chain Era (2009–2022)
In the early days of the industry (2009–2017), wallets were extremely difficult to use, even requiring local node operation. We will skip this stage directly.
Once usability improved, self-custody became the first choice—after all, in a decentralized world, "default distrust" is the foundation for survival. Well-known products such as MetaMask, Phantom, Trust Wallet, and OKX Wallet were all outstanding during this period.
From 2017 to 2022, the market ushered in a boom of public chains/L2s. Although most chains still used Ethereum's EVM architecture, making a compatible and good tool was enough to meet demand.
During this period, the core positioning of wallets was as "good tools." Although the industry could see the commercial prospects of traffic entry and DEX entry, security, ease of use, and stability were the first requirements.
However, from 2023 to 2025, the situation changed. Solana, Aptos, BTC (inscription period), and other heterogeneous public chains completely captured the user market. Although Sui itself developed well, after a hacking incident, large funds became hesitant due to the drawbacks of excessive centralization.
Driven by the financing era of "fat protocols, thin applications," although VCs made little profit, the market structure did indeed change.
2.2 Second Stage: Multi-Chain Era (2022–2024)
Faced with a multi-chain landscape, even established players like MetaMask had to transform and begin to natively support Solana, BTC, etc. Leading players such as OKX Wallet and Phantom had already achieved multi-chain compatible architectures early on.
The core sign of multi-chain compatibility is how many chains are supported, and where transactions are sent from—this means the backend does a lot of work, and the client only handles signing. From the user's perspective, it's about whether you need to find an RPC node yourself to use the wallet.
Now, multi-chain compatibility has almost become standard. Persisting with a single chain for the long term is difficult to sustain, as the hot spots of chains are constantly changing.
A typical case is the Keplr wallet, which focuses on the Cosmos ecosystem, but this track has never really taken off. Many application chains quickly built on Cosmos gradually became inactive after launching. As the threshold for building EVM L2s gets lower, the situation for single-chain wallets may ease, but their ceiling is also there.
After basic tools became easy to use, users began to awaken commercial needs within wallets!
True asset owners not only want to custody assets but also actively drive them—seeking the best yield venues and choosing interaction targets. But users are also tormented by the complexity of various DApp interactions and must always beware of phishing sites. Since that's the case, why not use built-in wallet features directly?
2.3 Business Competition Branch Period
The focus of competition among wallets shifted to the business level, typically with aggregated DEXs and aggregated cross-chain bridges. Although Coinbase explored integrating social features, this demand was too much of a pseudo-need and never really took off.
Returning to rigid demand, users need to complete multi-chain asset transfers at a single wallet entry point. At this time, coverage, speed, and slippage become the core competitive points.
The DEX field can further extend to derivatives trading: RWA (such as stock tokenization), Perps (perpetual contracts), prediction markets (which will be hot in the second half of 2025, since the World Cup will be held in 2026). Parallel to DEXs is the demand for DeFi yields.
After all, on-chain APY is higher than in traditional finance:
Coin-denominated strategies: ETH staking yields about 4% APY, Solana staking + MEV yields about 8% APY (for details, see the ten-thousand-word research report: The Evolution and Merits of MEV on Solana), and more aggressive strategies can participate in liquidity pools (LP), cross-chain bridge LPs (for details, see: Super Intermediary or Business Genius? Revisiting LayerZero, the Cross-Chain Bridge Leader, from V1 to V2 over the Past Year)
Stablecoin strategies: Although yields are relatively low, combining with loop leverage operations can improve APY. So by this year (2025), at the peak of business competition, wallet infrastructure is once again being upgraded. The reason is that the above transactions are too complex—not just in transaction structure, but also in transaction lifecycle complexity.
To achieve truly high yields, automated trading is needed: dynamic rebalancing, scheduled limit orders (not just market orders), DCA, stop-loss, and other advanced features. But these features were impossible to implement in the pure self-custody era. So, should it be "security first" or "profit first"? Actually, it's not a difficult question, because the market naturally has different needs.
Just like during the rampant Telegram Bot era, many players handed over their private keys in exchange for automated trading opportunities—a high-risk model of "if you're afraid, don't play; if you play, don't be afraid." In contrast, major service providers must consider brand and reputation when making wallets. So is there a solution that can securely custody private keys and relatively ensure that service providers won't run away? Of course! This brings us to this year's upgrade in underlying custody technology.
3. Underlying Custody Technology Upgrade Period
Returning to the underlying technology upgrade mentioned at the beginning, let's analyze them one by one.
3.1 Farewell to the Era of Complete Self-Custody
First, as pure wallet vendors, Metamask and Phantom's moves are relatively lightweight, more experience-driven, because social login only solves user needs such as cross-device and recovery, and does not fully enter specific application-level tracks. However, their transformation is, to some extent, a farewell to the era of complete self-custody. Self-custody has degrees, but no one can truly define what is complete and what is incomplete.
First, self-custody itself means that the user's private key can only be stored on the user's device. But this has had many problems in the past. If the locally encrypted private key is compromised, there is a risk of brute force, and the strength depends on the user's password. When syncing across devices or backing up, you always have to copy it out, so the clipboard permissions of the operating system become a life-or-death line.
I remember clearly that a certain wallet vendor, on the page for copying the private key, only allowed the first part to be pasted by default, and the remaining digits had to be typed by the user, which directly led to a more than 90% drop in reported private key theft cases during that period. Later, hackers got smarter and brute-forced the remaining digits, which led to another round of confrontation.
After Ethereum's Prague upgrade, due to the extremely high permissions of 7702 and the obscure nature of signatures, as well as the special nature of potentially affecting the entire chain, high-phishing-risk features like permit 2 were triggered again. So, the root of self-custody is that users can't easily get used to the industry background of fully controlling their assets.
After all, if the private key is with the user, that's naturally fine, but if an encrypted copy is left on the server to prevent the embarrassment of total asset loss if the user's local device is lost, can this still be considered self-custody? Metamask and Phantom's answer is: yes. But at the same time, the service provider must also be prevented from acting maliciously.
3.2 First, Metamask
Their approach is simple: the user logs in with an email and sets a password, and the two combine to form something called TOPRF (Threshold Oblivious Pseudorandom Function), which is used to encrypt the user's private key. The encrypted private key can naturally be backed up.
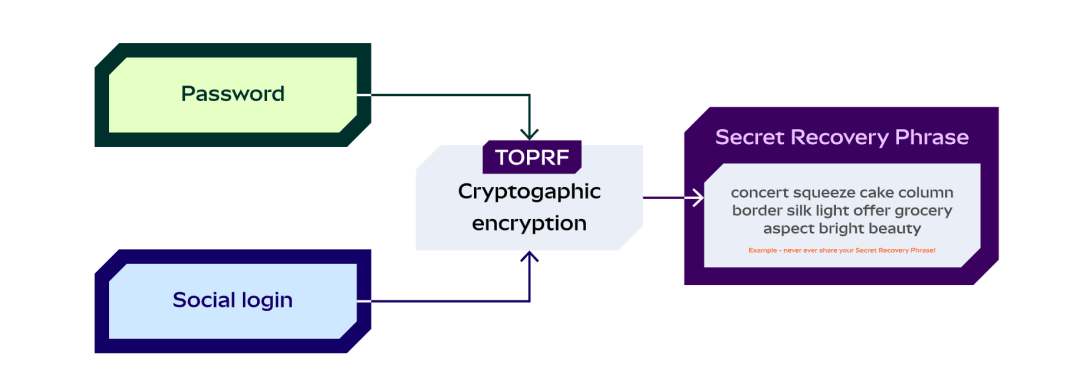
Then this TOPRF is distributed in shards using typical SSS (Shamir Secret Sharing) algorithm. These social login service providers obtain the encrypted data through social verification, and the user's password is also required to fully decrypt it.
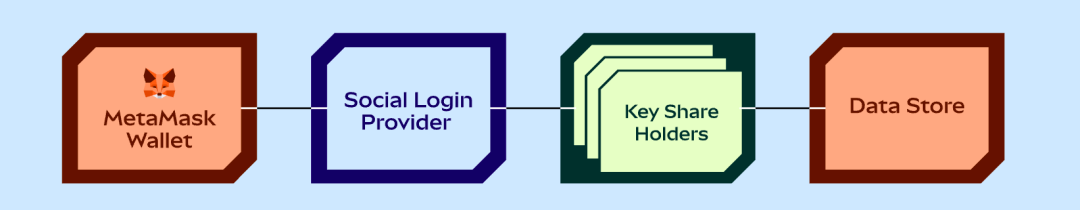
So the security risk is not completely eliminated, as weak passwords + email account theft are still risks, and if the user forgets the password, recovery is naturally impossible. But the benefit is greater convenience, and the experience is basically the same as web2.
3.3 Now, Phantom
Looking at the diagram, the overall architecture is more complex, but essentially it is still backend storage of encrypted private keys, with sharded management of the keys used for encryption and decryption.
The difference from MetaMask is that the key used for encryption is split into two parts, with one part stored by another service provider called JuiceBox Network. Social login + pin (4 digits) are required together to use its shard.
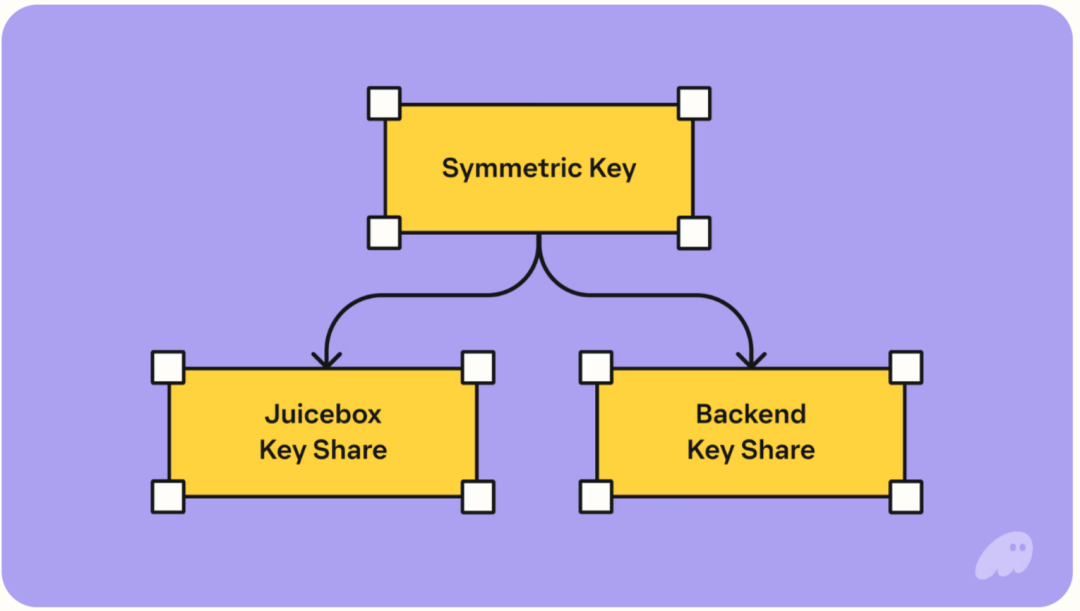
Overall, as long as the user's email is not stolen and the pin is not forgotten, recovery is always possible. Of course, in extreme cases, if JuiceBox and Phantom collude, they can also decrypt assets, but at least the attack cost for hackers increases from a single point to multiple parties. Moreover, since JuiceBox is a network, its security design is also distributed among multiple validators.
It can be said that in terms of social recovery, these two companies have made certain compromises while adhering to the bottom line, but for the sake of low-probability events, they have not suppressed user experience. I think this is a good change, as what the blockchain industry needs most is to embrace ordinary users, not force them all to become industry experts.
4. Self-Custody Using Trusted Execution Environment (TEE)
The previous social login can only solve the recovery problem, but not the problem of automated trading. Each company has a slightly different approach to this.
First, some background: TEE stands for Trusted Execution Environments. It is essentially still a server, but this server can ensure that its memory environment and running process cannot be read or interfered with, even by the AWS service provider or the server owner. In addition, after it starts running a program, it will publish a file called Attestation. The party interacting with the TEE can verify whether this document matches the open-source version it claims to run.
Only when the program it runs matches the specified open-source version will the two correspond, thus proving trustworthiness. This has already been widely applied in the industry: for example, Avalanche's official cross-chain bridge uses SGX (a TEE model) to run notary validators; on Ethereum mainnet, 40% of blocks are already produced using buildr net, which is also TEE-based; not to mention various financial banks, which strictly control against insider risks and have basically introduced TEE. Leading exchanges, under the compliance background of 2025, have also introduced TEE at high cost for hot and cold wallet signature custody.
Although there are many difficulties in using TEE, such as low machine performance (which can be solved with money), downtime risk (loss of memory information), and complex upgrades. The remaining question is how each exchange provider offers TEE services in wallets?
4.1 Coinbase and Bitget's Solution
At first, it is hard to imagine that Coinbase, a compliant exchange listed on the US stock market, would make the most centralized version. Bitget's logic and architecture are almost identical.
Essentially, they just use TEE to generate private keys and drive signature services. But how does TEE verify that this service truly reflects the user's intent? Coinbase is entirely based on user login, relying on backend authentication to forward instructions to TEE, which then completes the transaction.
Bitget is similar. Although there is little information, it appears that there is no signature page on the client side, and a new address with eip-7702 is set directly, thus achieving gas fee payment. The advantage of this setup is that at least the user's asset private key is indeed in the TEE, but whether the backend will insert other strange instructions cannot be proven or disproven.
Fortunately, there is evidence on-chain. So, I believe that Coinbase and others are essentially adding the reputation of the exchange, since whether the private key is exported is definitely recorded, which can rule out user insurance fraud. The only risk is the exchange acting maliciously, which is consistent with the underlying trust model of users trusting CEXs.
4.2 Bn and Okx
Comparing the MPC and SA of these two, the logic is essentially the same. In terms of driving transactions, OKX will pop up an intent authorization signature page, which, combined with TEE's internal intent verification logic, gives users a higher degree of authorization, but also increases the user's cognitive load.
Binance's MPC is more a result of its existing technical system (MPC actually has limitations in multi-chain expansion). After introducing TEE, users need to transmit a shard from their local device, encrypted, into the TEE. OKX, on the other hand, requires users to transmit their local mnemonic, encrypted, into the TEE.
As a user, there is no need to worry too much about security risks here. Reliable communication between TEE and the client is very mature, and theoretically completely prevents man-in-the-middle attacks. As long as asymmetric encryption is done with TEE's public key, only the private key can decrypt it. There are also some differences in experience, such as how long the MPC or private key is valid in TEE, how to renew, etc. These are engineering issues and will not be elaborated here.
Analyzing the design motivation, the main benefit of this design is to reduce migration costs and avoid the cold start problem of users having to migrate assets to experience new advanced features. For example, Coinbase's setup focuses on the payment track, allowing traditional e-commerce service providers without local private key management experience to call private keys via API for on-chain operations. Binance's setup is used for the CeDeFi track, making it easier for users who usually watch K-lines to directly operate and purchase on-chain assets on similar pages, ignoring gas, slippage, multi-chain, and other issues.
5. Conclusion
How should we evaluate the year 2025, and how should we view the future? I believe this year is a year of silence for wallets, but also a year of transformation. There is not much noise, but big things are being done quietly. In today's multi-chain environment, simply making a good tool is no longer enough to support a large-scale wallet team (and supporting infrastructure). It inevitably needs various value-added services for oxygen, and coincidentally, this year is also an explosion year for applications: the perps track is reborn, RWA (stocks), prediction markets, and payments are all picking up simultaneously.
The market is gradually moving from fat meme to diversified DEX demand. Moreover, meme is only because trading is too fast and the transaction volume is too high, making the market seem large, but in reality, it's always the same group of people playing, the hot spots are changing, but user growth is not significant. Combined with the new custody systems of each exchange, backed by their reputations and powered by TEE.
Moreover, in the big trend, AI will become stronger and so will AI trading. Previously, wallets were only prepared for humans, not for AI. So I see that next year there will be even richer application explosions, because the underlying infrastructure is more mature. There will definitely be a gap period, because the TEE setup is still the play of large exchanges, and they are unlikely to open up external entry points as freely as Coinbase.
In addition, using DEX is only a need for some users; there are even more users who just want to earn some stable money. Combined with various subsidies and airdrops during each company's promotion period, plus an APY, they are very satisfied. CeDeFi products that can capture on-chain yields will be the first landing point for many CEX users (to supplement, this mainly refers to CeDeFi with independent addresses, such as Bitget's shared address model cannot capture this).
Finally, this year has also seen many improvements in passkey cryptography technology. Although this article does not cover it, more and more public chains such as Ethereum and Solana have gradually integrated the R1 curve (the default supported by device passkeys) through precompiled contracts. So wallets combined with passkey are also a hidden trend (although recovery and cross-device sync are difficult, so there are not many good applications yet). After all, any product that can be streamlined for high-frequency needs will eventually have a place.
